Blockchain 101
The yellow paper
How to Time-Stamp a Digital Document
Stuart Haber and W. Scott Stornetta published a paper called “How to Time-Stamp a Digital Document “ which essentially has most of the features and ideas of todays blockchain are present in that paper.
A general definition can be given as:
“A blockchain is a continuously growing list of records, called as blocks, which are linked and secured using cryptography”
-Wikipedia
Which was later used into Bitcoin Ethereum and unfortunately “THE DARK WEB”
Santoshi Nakamoto is the guy who created the Bitcoin original implementation which is then referred and came many other coins which itself is kind of fully encrypted and used all around the world. There is something called as mining which is used to break the code and match the hash to get the minimum hashing value under radar.
If you are not able to understand the above no issues follow below. :)
what consists of a block?
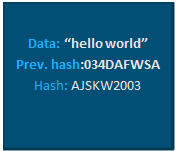
It has a DATA of course, PREVIOUS HASH which is kind of “from address” or where it stands and HASH which is the encrypted data.
Let’s say the above block is the block number one no other block is there behind it which is called as the GENESIS block. So, after creating this block which will never change ever and never for the eternity of life. This is no other block which will become one. The above block is always going to be the one and where other blocks originate
Genesis block
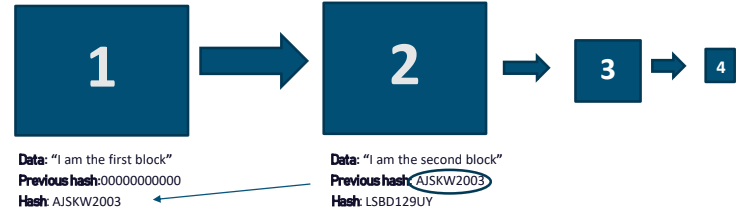
The chaining of the blocks which makes it cryptographically linked called as Blockchain.
Hash Crytography
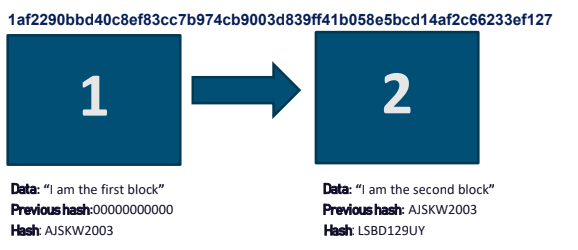
As you can see in the block number two which has the following data “I am the second block” which is having a hash value which represents the block .A change in the main data itself will cause avalanche effect
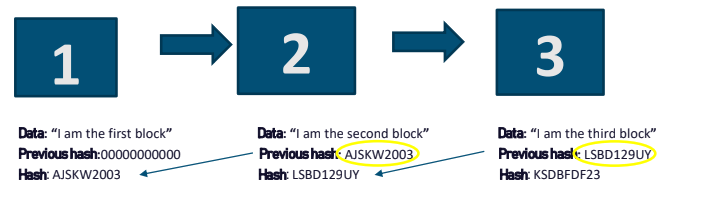
As you can see, we have this chain of values depends on the hash and previous hash which represents them. if someone tampers the data the position itself will get changes and there is a very less chance of data getting tampered. which we will see now …
The hash represents 64-character x 4 bits= 256 bits thus named as Secure Hash Algorithm 256(SHA256).
try here as you can see when you change a single character entire hash is changed thus called as avalanche effect.
Immutable ledger
Let’s say you bought a house near marina beach with pool and the document is submitted to the village government building and you also have a copy of the record. That is the only proof that the house belongs to you.
Traditional ledger

If someone comes and takes all the resources to tamper the data with your mutable ledger and makes it all his property there is no history no paper trail to prove it. YOU LOST.
Immutable ledger
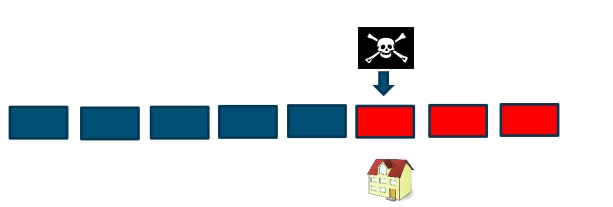
As per above image you can see that the on the following block the attacker attacked the block and changed the data which is reflected to progressive blocks. we can track what happened and can be reverted.
P2P network
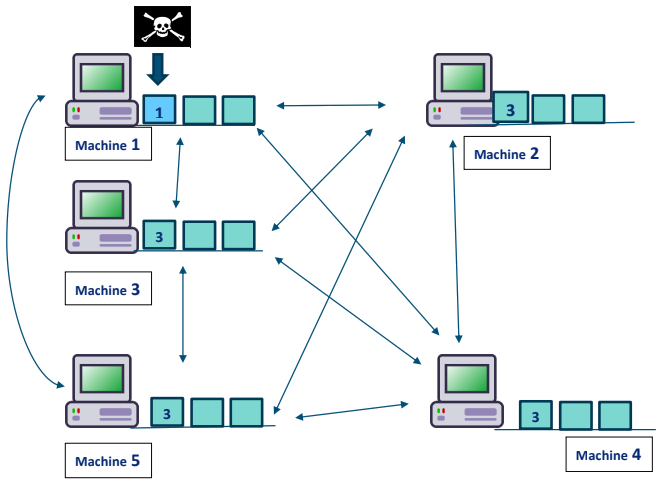
As you can the above is a decent description of the P2P network Rules
- The exact same iteration of data is spread out to all system.
- They all are in synchronously connected.
When the data is tampered as you can see above the data is changed to “1”. In machine 1. When other machines talk to the “machine 1” they all finds out the data is not proper in block 1 and all the machines start to create a voting kind of decision that who all has the data as “1” and who all has the data as “3”.
As per the voting the 3 wins which makes that the 3 is the original data and the “machine 1 block 1” is overridden. the data will be in thousands of systems which makes it practically unbreakable.
CONSENSUS PROTOCOL
The above voting system is called the consensus protocol which helps in keeping balance in the p2p environment and this protocol makes the data not getting tampered.
This protocol is kind of the heart of this system which takes care of the decision which data is the right to begin with.
Then the data is then balanced and every thing is back to normal
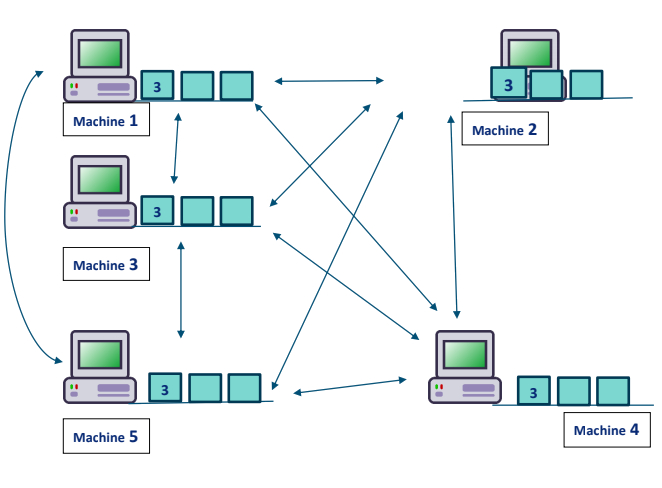
This is just basic understating of Blockchain. There is a lot more……


Comments (0)